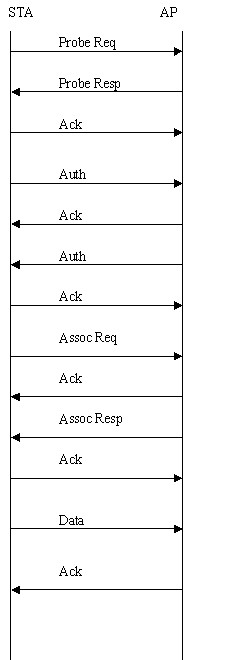
Figure: Handshaking between STA and AP
STA - Station
BSS - Basic Service Set, includes STA and AP
IBSS - Independent BSS
ESS - Extended Service Set, includes a few BSS
DS - Distribution System
Ad-hoc WLAN - forms IBSS
infrastrature WLAN - forms BSS
SSID - Service Set ID, an arbitrary string, thought of as the AP's name
BSSID - in infrastrature mode, it is AP Mac address; in IBSS, it is a random number, all are 6 bytes in length
802.11 frame format is more complicated than ethernet one. See figure below.
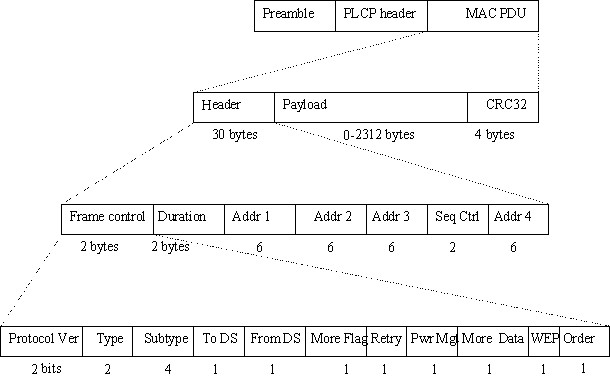
There are three types of MAC frames, namely:

Binding them altogether, the figure below shows the handshaking between STA and AP for an open-system authentication wlan network.

The original security mechanism of IEEE 802.11 standard was not designed to be strong and has proven to be insufficient for most networks that require some kind of security. Task group I (Security) of IEEE 802.11 working group has worked to address the flaws of the base standard and in practice completed its work in May 2004. The IEEE 802.11i amendment to the IEEE 802.11 standard was approved in June 2004 and published in July 2004.
Wi-Fi Alliance used a draft version of the IEEE 802.11i work (draft 3.0) to define a subset of the security enhancements that can be implemented with existing wlan hardware. This is called Wi-Fi Protected Access (WPA). This has now become a mandatory component of interoperability testing and certification done by Wi-Fi Alliance. Wi-Fi has information about WPA at its web site.
IEEE 802.11 standard defined wired equivalent privacy (WEP) algorithm for protecting wireless networks. WEP uses RC4 with 40-bit keys, 24-bit initialization vector (IV), and CRC32 to protect against packet forgery. All these choices have proven to be insufficient: key space is too small against current attacks, RC4 key scheduling is insufficient (beginning of the pseudorandom stream should be skipped), IV space is too small and IV reuse makes attacks easier, there is no replay protection, and non-keyed authentication does not protect against bit flipping packet data.
WPA is an intermediate solution for the security issues. It uses Temporal Key Integrity Protocol (TKIP) to replace WEP. TKIP is a compromise on strong security and possibility to use existing hardware. It still uses RC4 for the encryption like WEP, but with per-packet RC4 keys. In addition, it implements replay protection, keyed packet authentication mechanism (Michael MIC - Message Integrity Check).
Keys can be managed using two different mechanisms. WPA can either use an external authentication server (e.g., RADIUS) and EAP just like IEEE 802.1X is using, or pre-shared keys without need for additional servers. Wi-Fi calls these "WPA-Enterprise" and "WPA-Personal", respectively. Both mechanisms will generate a master session key for the Authenticator (AP) and Supplicant (client station).
WPA implements a new key handshake (4-Way Handshake and Group Key Handshake) for generating and exchanging data encryption keys between the Authenticator and Supplicant. This handshake is also used to verify that both Authenticator and Supplicant know the master session key. These handshakes are identical regardless of the selected key management mechanism. That means, only the method for generating master session key changes.
The design for parts of IEEE 802.11i that were not included in WPA has finished (May 2004) and this amendment to IEEE 802.11 was approved in June 2004. Wi-Fi Alliance is using the final IEEE 802.11i as a new version of WPA called WPA2. This included, e.g., support for more robust encryption algorithm (CCMP: AES in Counter mode with CBC-MAC) to replace TKIP, optimizations for handoff (reduced number of messages in initial key handshake, pre-authentication, and PMKSA caching).
802.1X plays a major role in this new standard. The 802.1X-2001 standard states:
"Port-based network access control makes use of the physical access characteristics of
IEEE 802 LAN infrastructures in order to provide a means of authenticating and authorizing
devices attached to a LAN port that has point-to-point connection characteristics, and of
preventing access to that port in cases which the authentication and authorization fails.
A port in this context is a single point of attachment to the LAN infrastructure."
--- 802.1X-2001, page 1.
802.1x provides a framework for user authentication over wireless LANs. The only minor change is to define how a "network port" exists within 802.11. The IEEE decided that an association between a station and an access point would be considered a "logical port" for the purpose of interpreting 802.1x. The successful exchange of Association Request and Association Response frames is reported to the 802.1x state engine as the link layer becoming active. 802.11 association must complete before the 802.1x negotiation begins because the 802.1x state machine requires an active link. Prior to a successful 802.1x authentication, the access point drops all non-802.1x traffic. Once the authentication succeeds, the access point removes the filter and allows traffic to flow normally.
The second change made possible by 802.1x is that the EAPOL-Key frame can be used to distribute keying information dynamically for WEP. Figure below shows a sample EAPOL exchange on an 802.11 network.
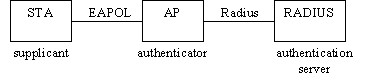
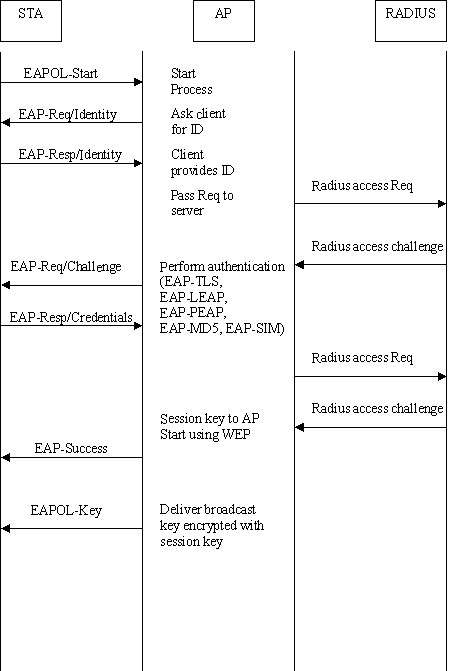
For small office / home office (SOHO), ad-hoc networks or home usage, a pre-shared key (PSK) may be used. When using PSK, the whole 802.1X authentication process is elided. This has also been called "WPA Personal" (WPA-PSK), whereas WPA using EAP (and RADIUS) is "WPA Enterprise" or just "WPA".
The 256-bit PSK is generated from a given password using PBKDFv2 from [RFC2898], and is used as the Master Key (MK) described in the key management regime below. It can be one single PSK for the whole network (insecure), or one PSK per Supplicant (more secure).
This talks about the handshake for generating and exchanging data encryption keys between the Authenticator and Supplicant.
To enforce a security policy using encryption and integrity algorithms, keys must be obtained. Fortunately, 802.11i implements a key derivation/management regime. See figure.
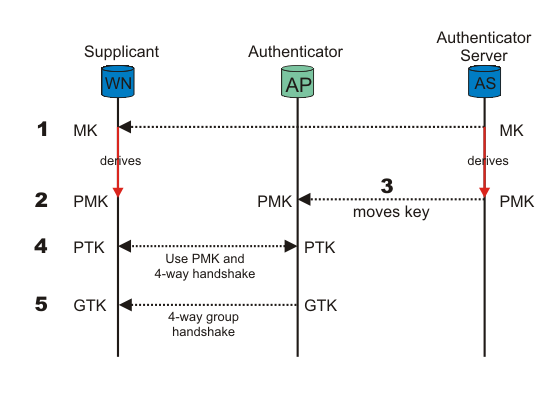
Figure KM: Key management and distribution in 802.11i.
When the Supplicant (WN) and Authentication Server (AS) authenticate, one of the last messages sent from AS, given that authentication was successful, is a Master Key(MK) (for WPA Enterprise). After it has been sent, the MK is known only to the WN and the AS. The MK is bound to this session between the WN and the AS.
Both the WN and the AS derive a new key, called the Pairwise Master Key (PMK), from the Master Key.
The PMK is then moved from the AS to the Authenticator (AP). Only the WN and the AS can derive the PMK, else the AP could make access-control decisions instead of the AS. The PMK is a fresh symmetric key bound to this session between the WN and the AP.
PMK and a 4-way handshake are used between the WN and the AP to derive, bind, and verify a Pairwise Transient Key (PTK). The PTK is a collection of operational keys:
Key Confirmation Key (KCK), as the name implies, is used to prove the posession of the PMK and to bind the PMK to the AP.
Key Encryption Key (KEK) is used to distributed the Group Transient Key (GTK). Described below.
Temporal Key 1 & 2 (TK1/TK2) are used for encryption. Usage of TK1 and TK2 is ciphersuite-specific.
See figure for a overview of the Pairwise Key Hierarchy.
The KEK and a 4-way group handshake are then used to send the Group Transient Key (GTK) from the AP to the WN. The GTK is a shared key among all Supplicants connected to the same Authenticator, and is used to secure multicast/broadcast traffic.
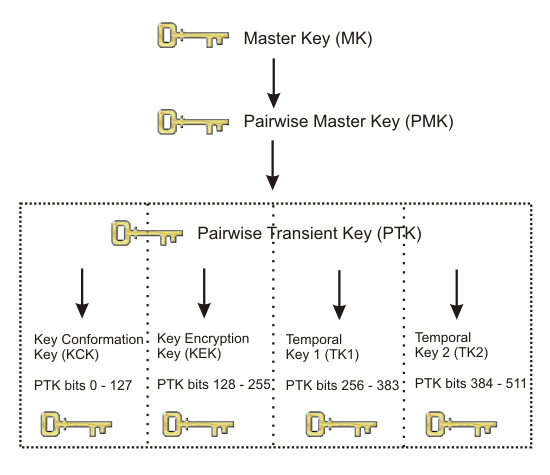
Figure PKH: Pairwise Key Hierarchy
Madwifi stands for Multimode Atheros Driver for Wifi. It is an open source wifi driver on Linux. As we speak now (27 June 2005), it requires at least Wireless Extensions 14 or better ( version 16 preferred). Wireless Extensions 16 is built into kernel version 2.4.23. Madwifi also requires Crypto API support enabled in kernel. Moreover, Madwifi requires sysctl support (Under General Setup). Originally, kernel 2.4.18 comes with Wireless Extensions v12 built-in.
1. modify the TOOLPREFIX in madwifi/hal/public/<arch>-<endiannness>-elf.inc eg. mips-le-elf.inc 2. export TARGET if you cross-compile eg. export TARGET=mips-le-elf (This is to set the madwifi/Makefile.inc "$TARGET" variable) 3. make KERNELPATH=<kernel path>
After compilation, we obtain object module, such as ath/ath_pci.o, ath_hal/ath_hal.o and net80211/wlan.o. Using insmod, we can load the object module into memory.
iwconfig ath0 mode master
iwconfig ath0 essid paradiso
iwconfig ath0 channel 9
iwpriv ath0 mode 2
ifconfig ath0 up
Hostapd is a user space daemon used for access point. It supports separate frontend programs, and an example text-based frontend, hostapd_cli is provided. In this example, for testing purpose, hostapd-0.4.1 is used together with wpa_supplicant-0.4.1 and madwifi-bsd version.
To compile hostapd, following the steps below:1. copy defconfig to .config, modify it to use correct path. -- enable madwifi CONFIG_DRIVER_MADWIFI CFLAGS += -I/..../madwifi-bsd -- disable bsd #CONFIG_DRIVER_BSD=y -- setup the openssl library path CFLAGS += -I/home/yeosv/ssl/include LIBS += -L/home/yeosv/ssl/lib 2. modify Makefile CC=mipsel-linux-gcc DIR_WPA_SUPPLICANT=../wpa_supplicant-0.4.1 3. compile it, and load the following madwifi modules, request_module() kernel call will require the following two modules. wlan_xauth.o wlan_tkip.o 4. execute in debug mode hostapd -ddd hostapd.conf
Here is a valid hostapd.conf example.
interface=ath0 driver=madwifi logger_syslog=-1 logger_syslog_level=2 logger_stdout=-1 logger_stdout_level=2 debug=0 dump_file=/tmp/hostapd.dump ctrl_interface=/var/run/hostapd ctrl_interface_group=0 ssid=MyWireless macaddr_acl=0 auth_algs=3 eapol_key_index_workaround=0 eap_authenticator=0 pwn_ip-addr=127.0.0.1 wpa=1 wpa_passphrase=secretpass wpa_key_mgmt=WPA-PSK wpa_pairwise=TKIP wpa_group_rekey=800 wpa_gmk_rekey=86400
wpa_supplicant is a WPA Supplicant for Linux, BSD and Windows with support for WPA and WPA2. wpa_supplicant is a daemon program that runs in the background and acts as the backend component controlling the wireless connection. wpa_supplicant supports separate frontend programs and a text-based frontend (wpa_cli) and a GUI (wpa_gui) are included with wpa_supplicant.
To compile wpa_supplicant, follow the steps below:1. copy defconfig to .config, modify it to use correct path CFLAGS += -I/home/yeosv/ssl/include LIBS += -L/home/yeosv/ssl/lib CONFIG_DRIVER_MADWIFI=y CFLAGS += -I/...../madwifi-bsd 2. modify Makefile CC=mipsel=linux-gcc CFLAGS=+=........ -I../hostapd-0.4.1 3. compile it, and execute wpa_supplicant -Bw -c/etc/wpa_supplicant.conf -d -iath0Here is a sample wpa_supplicant.conf file.
network={
ssid=Buffalo
key-mgmt=WPA-PSK
psk="secretpass"
priority=5
pairwise=TKIP
group=TKIP
}
WDS stands for Wireless Distribution System. Usually WDS is used between Access Points to allow transparent bridging of two ethernets over a wireless link.
To transparently bridge two wired networks over WLAN, the official solution is to use the 4 address capability of the IEEE 802.11 spec. This way one will have 2 sets of MAC addresses. One set is used between the 802.11 Station and AP, the other set will give the impression to the two hosts on the other interface (usually a copper Ethernet connection) that there is no intervening media change.
The difference between AP-STA mode and WDS mode: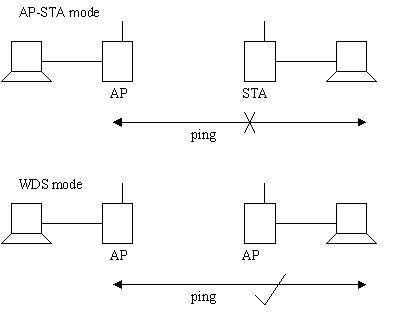
In AP-STA mode, the PC behind the STA cannot ping the AP, as AP will drop the packets which has PC as the sending Mac address. It is because STA is associated to the AP using its own Mac address. In WDS mode, the PC behind the WDS AP can ping another AP, as the packets use WDS AP Mac as the sending Mac address.